That work was not available when GrapheneOS was developed
What do you mean ? This has nothing to do with GrapheneOS in the first place (which by the way has been created in 2014. The article i linked refers to 2021).
I still consider it a black box.
Reverse engineering is a thing. It always has been. If every piece of closed source was a blackbox how can you explain exploitation ? How can bad actors exploit Windows, MacOS, CPU firmware and so on ? Your argument here is not practical. Also, why should Google put a backdoor inside a chip ? They already get every information they what directly from the people agreeing to use their software. So, why bother ? Moreover, every phone on the market has closed source firmware.
The Titan security chip is not a black box. The Titan M1 gas been scrutinazed by blackhat: https://dl.acm.org/doi/fullHtml/10.1145/3503921.3503922
Just because something is not open source does not mean you can't verify it (no, i'm not shilling closed slurce; no i don't think closed > open; no i don't think closed source is more secure)
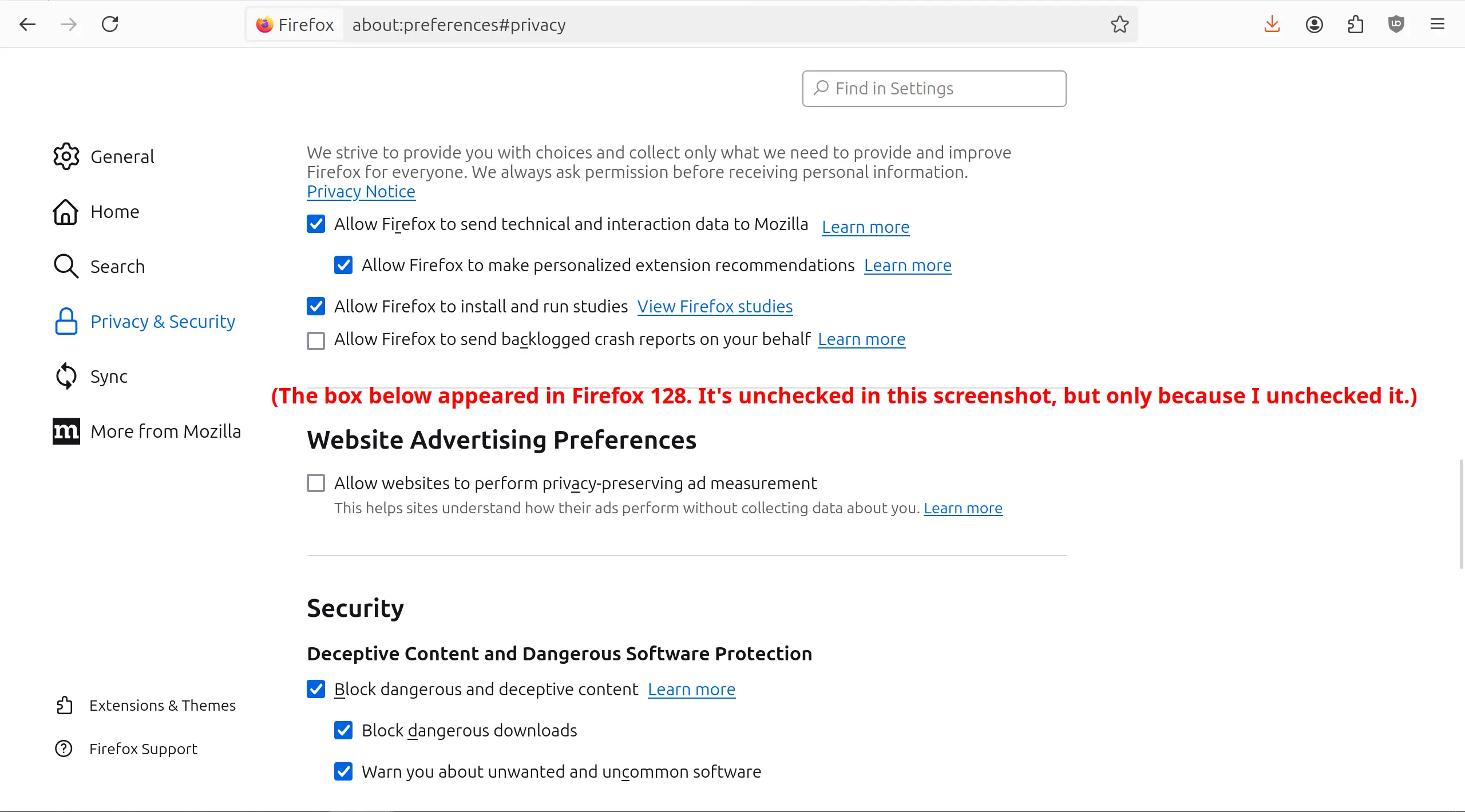
Firefox added ad tracking and has already turned it on without asking you
Attached: 1 image So this, from Firefox, is fucking toxic: https://mstdn.social/@Lokjo/112772496939724214 You might be aware Chrome— a browser made by an ad company— has been trying to claw back the limitations recently placed on ad networks by the death of third-party cookies, and added new featu...
Strong passwords are the key to protecting your organization's accounts - even the accounts you've forgotten about. Learn from Specops Software about securing test accounts and environments before they are breached.

Google Maps is testing a new ad format that gives users the option to add a stop for a sponsored location during navigation.
Popular encrypted messaging app Signal is facing criticism over a security issue in its desktop application. Researchers and app users are raising

Twilio has updated its iOS Authy two-factor authentication app following a hack that reportedly saw 33 million cellphone numbers being stolen.

Create docs and collaborate in real time on documents knowing they are end-to-end encrypted.
Fasten your seat belts, secure your tray table, and try not to give away your passwords

The first-in-the-nation law in Colorado includes biological or brain data in the State Privacy Act, similar to fingerprints if the data is being used to identify people.

Unless you've got a lawyer, that is

I use Florisboard. Noce keyboard!
Ads in Windows 11 settings are coming next month

The complaint claims that Babeland and Good Vibrations websites uses Microsoft's Clarity tracking software to see what visitors searched for and bought.

Earlier this year, the Federal Trade Commission warned that companies would be sorely tempted to change the terms and conditions of their privacy statements to allow them...

Temu "surprised" by the lawsuit, plans to "vigorously defend" itself.

Full-service Poseidon info stealer pushed by "advertiser identity verified by Google."

Those sites aren't really useful. If your threat model requires "hiding your fingerprint" you can use Tor Browser.
The major June update and a follow-up OSM data-only update (with a hotfix for the iOS app hanging) were successfully published and are available in all app stor…
The most common argument used in defense of mass surveillance is ‘If you have nothing to hide, you have nothing to fear’. Try saying that to women in the US states where abortion has suddenly become illegal. Say it to investigative journalists in authoritarian countries. Saying ‘I have nothing to h...

The Medusa banking trojan for Android has re-emerged after almost a year of keeping a lower profile in campaigns targeting France, Italy, the United States, Canada, Spain, the United Kingdom, and Turkey.

The Medusa banking trojan for Android has re-emerged after almost a year of keeping a lower profile in campaigns targeting France, Italy, the United States, Canada, Spain, the United Kingdom, and Turkey.

Why ? Just why ?
I completely agree with you. I think people downvoting me because "fuck Google" when in fact, hardware wise, is the best available to achieve privacy and security.
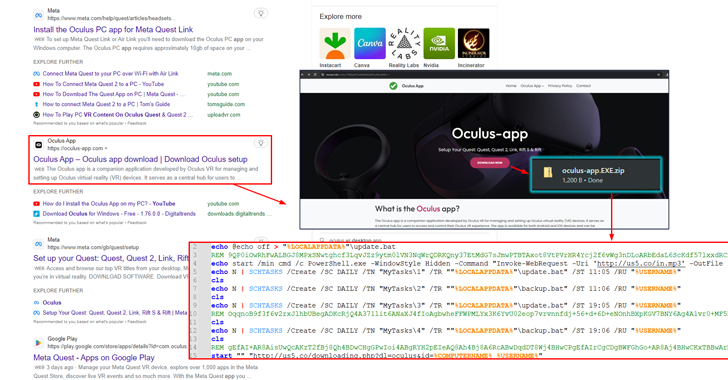
Discover how AdsExhaust adware targets Meta Quest app users, manipulates browsers, and generates unauthorized revenue through sophisticated techniques
Yeah, it's a shame. Only Google seems to take updates seriously.
PSA: always update your smartphone | Ratel RAT targets outdated Android phones in ransomware attacks
An open-source Android malware named 'Ratel RAT' is widely deployed by multiple cybercriminals to attack outdated devices, some aiming to lock them down with a ransomware module that demands payment on Telegram.

Nore information at: https://grapheneos.org/features#duress
Nice to see it!
Luckily GrapheneOS has a duress passowrd feature. Very useful for these situatuons!
Disabling updates is not a good choice. If you use Windows, update Windows. Having an insecure and not up to date version of windows makes you more vulnerable
Braxman's content is pure scam
I personally blocked him and it was one of the best decision of my digital life. He's basically wasting his life spreading misinformation about GrapheneOS. He's simply too much to handled for my mind. Without seeing him, i feel this place is much more relaxing and useful to see it.
I think this question has some sort of relativity. What is your threat model ? Are you trying to protect your data from the service itself, fromyour mom, from the police ? You want anonimity ? And so on.
There is no an ultimate answer to this question. For example, i'm using WhatsApp because it fits my threat model (messages are encrypted, metadata is not but for me is fine). Then, i use Signal with people that use Signal (where i live, 99% of people use WhatsApp).
I would never use Telegram since is not encrypted by default.
If i was you, i would buy a Google Pixel 8 (8a is cheaper than 8 and 8 pro). They all provide support for GrapheneOS, have 7 years of updates, MTE, and so on
For context: https://grapheneos.org/faq#device-support
GrapheneOS!
Yes you can! Your offline backup is inside the app data (you need a file manager to access the folder). If you use a Samsung Device, i think you won't be able to see it unless you plug the phone on your PC.
Hi! One thing you could consider is using GrapheneOS which supports Android Auto without special priviliges!
Hi! I know this option doesn't respect the second point of your list. That beijg said, if i was you i would buy a Google Pixel 7 or 8 and then i would put GrapheneOS on it!