In the style of Higginbottom. Formerly staticv0id@reddit
In 2011 I was aghast when I learned a popular keycard / biometric system used FTP to pull down its cleartext list of acceptable keys from the server.
The username was something like ADMIN and the password was PASS.
And no, that wasn’t the FTP command; that was the password.
So I’m not surprised that there are still problems with these devices.
edit: more complete thought
Pocket Ad Machine
Sellfone
Social Distorter
Dynamic Uniform Radio Receiver (DURR)
Tactical Nuclear Penguin has entered the chat. 32%
Thanks for mentioning it, I plan to join today!
Can hardly believe I’m not alone.
On Thursday, I met with a therapist who ran through the ACES inventory with me during our session.
It’s been a wild ride since then. Never have I felt so much validation and relief, and never have I wanted to get started with the healing process so much. At long last, there’s a name for what I’ve felt over the past 36 years, and more importantly there’s a treatment protocol.
I truly thought I was alone, especially after my encounter with a different therapist some 20 years ago. No one was talking about c-PTSD back then.
Yesterday I could hardly sleep, as it often happens. I let my emotional dysregulation (learned that has a name too!) run wild, intentionally, to pull together a list of all the traumas I faced. I could scarcely sleep until I had written everything down.
Just sharing my joy at being understood.
The Secretary of the Interior is a Native American. She would know better than any non-Native museum curator what should be done with Native artifacts.
Let the tribes decide how to tell their stories.
… and the credulous 33% of the population?
Needs more drama, pancake makeup, and Monster High dolls.
Thank you! You explained it really well.
You're welcome!
As I understand it, most of the physical infrastructure for data transmission belongs to some private company. These companies sell the usage rights to smaller companies and so on. So these companies are the ISPs.
Usually they are ISPs. If you wanted to buy a route on a fiber optic cable (usually called "dark fiber" in this context), it's just a different product that they sell. There's no Internet access on a dark fiber link, not even light from a router at the other side. If you were to purchase a dark fiber route, you'd have to provide routers at either end and light that path yourself.
Whomever owns those ISPs also owns that infrastructure. In liberal countries, it's usually a for-profit company, but could be a non-profit as well. In less liberal countries, the government may own and operate the fiber.
In this sense, you would either have to build your own network infrastructure (cables, routers, switches) or rent the infrastructure from the owners.
Correct.
The physical infrastructure is basically largely independent of the protocols that run through it (optical cables simply carry light). Couldn’t this infrastructure then somehow be used as a direct connection between two users via a protocol other than IP?
Absolutely. CLNS, IPX, Appletalk, DEC Phase V, and Banyan VINES are all older examples of layer 3 protocols that work perfectly fine over fiber. Once upon a time, IPX was more dominant than IP in businesses. I ran a dual-stack IPX and IP network 25 years ago.
These other layer 3 protocols do not interoperate with IP. For example, on my IPX and IP network, I had computers that could only speak IPX. None of those were able to communicate with IP networks at all. They did not know anything about the Internet, could not use it, could not access it. A web browser on these machines would simply not work.
That's true for routers as well. If I were to order an Internet circuit, and I enabled IPX on my router, IPX would not work across that link because the ISP doesn't support IPX. Both ends must agree to route the layer 3 protocol.
But IP won out in the long run. Not because it was government or corporate owned, not because it was centralized, not because it was engineered to be unfair. It won out because it wasn't any of these things.
The standards for Internet protocols are openly developed by a body known as the Internet Engineering Task Force (IETF). Anyone is free to look at the specs, known as RFCs; anyone is free to write their own implementations of the protocols. This includes IP, TCP, UDP, BGP, DNS, HTTP, HTTPS, and other helper protocols like DHCP and ARP.
That's why there is a such a diverse, worldwide marketplace of router hardware/software vendors. Each of these vendors have developers that used the RFCs to write their particular implementation of router software.
Going back to the question of neutrality, the RFCs themselves neither encourage nor discourage neutrality. They exist as an agreement on how to exchange information: how packets are constructed, what information is included, how software ought to interpret that info, and so on. It is up to the router vendors to implement these standards, and it is up to the ISPs who buy those routers how to handle those packets.
The ISPs may enforce policies that are handed down from the jurisdiction where they operate. The ISPs may even be owned and operated by the government. China's Great Firewall is a prime example of anti-neutrality. Iranian Internet, I understand, is also government run and heavily monitored. These providers will use information in the IP packets to throttle or even block that communication.
In more liberal countries, most neutrality proponents are concerned primarily with quality of service. For example, they argue that Comcast Universal should not throttle or de-prioritize traffic to Netflix because it is a competitor to Comcast's own streaming service.
In either case, the protocol spec itself is not the reason for anti-neutrality behavior by these organizations. And switching to another layer 3 protocol, whether it's one that already exists or has yet to be invented, won't facilitate that neutrality by itself.
There's a fair bit to unpack in this comment.
Easier one first. ICANN was removed from US Dept of Commerce oversight in 2016. They are a stand-alone non-profit entity. From the linked article:
"The contract regarding the IANA stewardship functions between ICANN and the National Telecommunications and Information Administration (NTIA) of the United States Department of Commerce ended on October 1, 2016, formally transitioning the functions to the global multistakeholder community."
ICANN manages global DNS, the name service that translates my Lemmy instance's name to an IP address my computer can use to contact the server. It is not "the Internet" per se. It is an important service run on the Internet.
Second: ISPs create the Internet by connecting to one another. There is no connecting to "the physical backbone" without connecting to another ISP. There isn't any single "backbone" or other notional central point. There's no neutral entity operating the biggest router or backbone in the world where neutrality reigns supreme. There's no big bundle of fiber encircling the globe where everyone puts their packets.
The CAIDA visualizations are a great way to look at the interconnections that make up the Internet. The first graph on that page is what the Internet looks like in terms of "the backbone". It's really a mesh of connectivity among the largest ISPs in the world. The red center of the graph shows the most dense interconnections. That's where the term Internet comes from - an internetwork, or network of networks.
They must connect together because physical access to fiber is not enough. They must connect physical fiber to router equipment that is able to 1) send an enormous quantity of packets among each other and 2) communicate reachability for the different networks using BGP.
By the way, those segments of physical fiber only connect two devices together at a time. Hence the mesh in the CAIDA diagram.
That is the true nature of the Internet. Without those interconnections and routers, you have islands of connectivity that cannot reach each other.
It's like your example in the earlier comment with the experimental protocols. You could build your own network without some connection point to the larger Internet. You could do it with any set of protocols you wished -- your network, your rules. But without a connection to an ISP, it would not be able to reach Internet resources. Your network would simply be an island.
I mean, you could make it a great island with lots of services, and your island could have a big signpost that says "Free and Neutral Forever". But it would still be isolated from the Internet.
Source: I work on telecom / ISP networks.
I am not sure what you mean by eliminating “gatekeeping.” ISP’s route your IP packets for you in exchange for money. ICANN provides a hierarchy for name services via DNS. You could choose not to use DNS or an ISP, but either choice would make accessing common Internet services impossible.
The experimental protocols you mentioned are routing protocols. Routing protocols communicate reachability information for groups of IP addresses, known as “prefixes.” IP itself is a routed protocol, like any layer 3 protocol in the OSI model. It provides a standard by which computers can communicate across a large internetwork.
It is possible that a peer-to-peer routing protocol would enable you to access the Internet without a network connection of your own. But for that service to be useful, someone somewhere in the mesh would have to connect to the rest of the global Internet through a service provider. Otherwise your network is isolated, like a group of desktop computers plugged into a standalone switch, with no router to send packets to the Internet.
What specifically do you find objectionable with ISPs or ICANN?
Most of these are VPN technologies of one sort or another. These sit on top of layers 3 or 4 and encapsulate IP packets.
In other words, each packet sent to your internet provider has two sets of IP addresses. The outer set is to communicate between your computer and the VPN termination point. The second, inner set is between your computer and the service you are ultimately using.
Web traffic almost always uses HTTPS for transport, Usenet NNTP.
OSI layers 5 and 6 are not relevant in modern IP networks. If they are needed, they are provided in the application layer.
Depends on the cloud provider. AWS, as an example, have up to three “availability zones” within a single data center. If the customer needs HA, they are encouraged to run their applications in separate availability zones. It means different subnets within the VPC, redundant LBs spread across those zones, and more.
There is also probably DNS-based global load balancing across different data centers.
That’s just the hosting infrastructure. I’m sure Chujo works on the office LAN as well. He might wear the infosec hat also, which means he’s up to his eyeballs in firewall policy.
I don’t envy my brethren in software development orgs. Been there, done that, got that t-shirt long ago.
This is a software development business, which is a positively bananas trade no matter what’s getting written. And the smaller the business, the more hats network guys wear. We work with everything from the server app down to the coffee machine fueling the devs. And 100% uptime isn’t the most crazy demand I’ve heard. I’m sure Chujo is busier than a one-armed paper hanger with jock itch.
At least he’s got money to throw at his hosting company. Scaling up would have been much slower in the old days.
Container for smaller objects.
IEC C13 socket with C14 locking plugs. Already ubiquitous in data center facilities. Rated for voltages between 110 and 250, so it works for any country’s common household current.
Tools you’re not sure you’ll need. Harbor Freight tools are super cheap and flimsy, but may be the right choice if you’re not using them often.
If you find yourself using a cheap tool all the time and hating the quality of it, then it’s time to buy something better.
Science exists to figure out what really, actually does work. Smart people were still figuring that out at the turn of the last century.
Most smart people have figured it out now. Dumb people are still not testing their ideas.
I read that title in the original early 1980’s Times New Roman ad font.
Sailor Moon selling used cars


Inspired by Sailor Mustache, who was a local Sailor Moon cosplayer with severe five o'clock shadow and cigar. He was huge in Japan.
Network gods in the heavens, surrounded by router pucks, eating network cable spaghetti


An offering to Them against router issues this Turkey Week.
Old Goth Rivetheads On Elliptical Machines
GET YOUR ASS CRANKIN TO SPOOKY GOODNESS SO YA FIT IN THEM BONDAGE PANTS AGAIN
Starfield alternate soundtrack

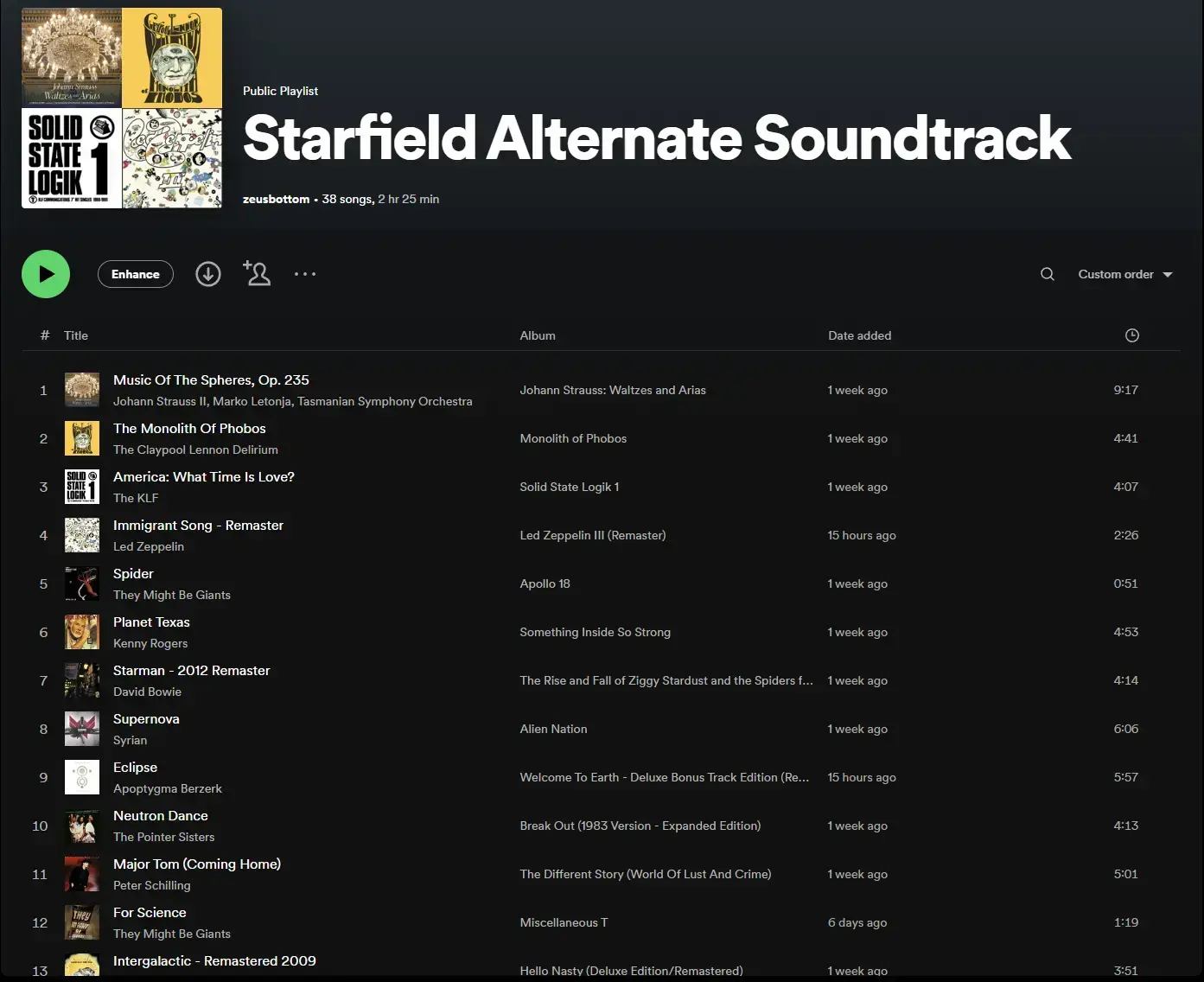
Kenny Rogers, Zeppelin, Bowie, Tom Waits, KLF, Rob Zombie, They Might Be Giants, Pointer Sisters, Muse, and of course Alestorm.
edit: playlist URL here
To Commander Ikande
"Look me in the eyes and tell me why you did it."
You should fucking know, Commander. 500 credits. That's why.
Remember when you pulled me aside and sat me down for our little chat through the glass? I told you, all I wanted to do was pay my 500c bounty and go.
You said, no, not this time.
You said, I want dirt on the Fleet.
You said, I want to take down the Fleet, and you're going to help me.
You know what they say about negative bias, and that was a real fucking negative introduction.
That brings us to now, with my gun pointed at your head, my new associates eyeing gleefully their new quarters aboard this august vessel.
Look me in the eyes, motherfucker. Because I like that look when you realize you vastly fucked up. Your command is ours now. Half your men are dead, the other half in lifeboats.
All over 500 credits.
Boys, haul him off.
What is the equivalent to CLLI codes outside of North America?
CLLI codes are location identifiers used throughout North America to describe physical spaces.
Does something similar exist anywhere else in the world?
