Explore the Kubernetes scheduler implementation principles and how you can define your own scheduling logic by implementing interfaces defined by extension points.
I have an apostrophe and it’s super annoying as some companies see it as a SQL injection hack and sanitize it.
My surname contains a character that's only present in the Polish alphabet. Writing my full name as is broke lots of systems, encoding, printed paperwork and even British naturalisation application on Home Office website. My surname was part of my username back at uni, and everytime I tried to login on Windows, it would crash underlying LDAP server, logging everyone in the classroom out and forcing ICT to restart the server.
It was my turn to post it this week
I would like to confine it to firms using AI recruiting tools
and actively do damage to companies that don't.
Just like everyone, they want more users, so their code runs on more machines, more reported bugs, better quality.
This article is part of a series on (European) innovation and capabilities. This is a lightly edited transcript of my presentation today at the ACCSS/NCSC/Surf seminar ‘Cyber Security and Society’. I want to thank the organizers for inviting me to their conference & giving me a great opportunity to ...
Explore whether adding the K8S CPU limit will degrade service performance.
Explore whether adding the K8S CPU limit will degrade service performance.
tl;dr: Having swap is a reasonably important part of a well functioning system. Without it, sane memory management becomes harder to achieve.

To be clear, I don't blame the poster of this comment at all for the content of their post – this is accepted as "common knowledge" by a lot of Linux sysadmins and is probably one of the most likely things that you will hear from one if you ask them to talk about swap. It is unfortunately also, however, a misunderstanding of the purpose and use of swap, especially on modern systems.
I'm not sure if you understand what swap actually is, because even machines with 1Tb of RAM have swap partitions, just in case read this post from a developer working on swap module in Linux https://chrisdown.name/2018/01/02/in-defence-of-swap.html
Creating Asynchronous Applications with Virtual Threads Venkat Subramaniam BackEnd

YouTube Video
Click to view this content.
Continuations: The magic behind virtual threads in Java by Balkrishna Rawool @ Spring I/O 2024

YouTube Video
Click to view this content.
This document presents new time-based UUID formats which are suited for use as a database key. A common case for modern applications is to create a unique identifier for use as a primary key in a database table. This identifier usually implements an embedded timestamp th...
This document presents new time-based UUID formats which are suited for use as a database key.
This specification defines the UUIDs (Universally Unique IDentifiers) and the UUID Uniform Resource Name (URN) namespace. UUIDs are also known as GUIDs (Globally Unique IDentifiers). A UUID is 128 bits long and is intended to guarantee uniqueness across space and time. UUIDs were originally used in...
This specification defines the UUIDs (Universally Unique IDentifiers) and the UUID Uniform Resource Name (URN) namespace. UUIDs are also known as GUIDs (Globally Unique IDentifiers). A UUID is 128 bits long and is intended to guarantee uniqueness across space and time. UUIDs were originally used in the Apollo Network Computing System and later in the Open Software Foundation's (OSF) Distributed Computing Environment (DCE), and then in Microsoft Windows platforms.
Even though we often hear terms like L1, L2, cache block size, etc., most programmers have a limited understanding of what cache really is. This is a beginner-friendly primer on how cache works.
Even though we often hear terms like L1, L2, cache block size, etc., most programmers have a limited understanding of what cache really is. This is a beginner-friendly primer on how cache works.
In this post, I look at Virtual Threads and if they are a silver bullet for blocking tasks.
The Linux kernel uses the CPU default scheduler, CFS,
Linux 6.6 (which recently landed on Debian) changed the scheduled to EEVDF, which is pretty widely criticized for poor tuning. 100% busy which means the scheduler is doing good job. If the CPU was idle and compilation was slow, than we would look into task scheduling and scheduling of blocking operations.
EDIT: Tried nice -n +19, still lags my other programs.
yea, this is wrong way of doing things. You should have better results with CPU-pinning. Increasing priority for YOUR threads that interact all the time with disk io, memory caches and display IO is the wrong end of the stick. You still need to display compilation progress, warnings, access IO.
There's no way of knowing why your system is so slow without profiling it first. Taking any advice from here or elsewhere without telling us first what your machine is doing is missing the point. You need to find out what the problem is and report it at the source.
The CPU is already 100% busy, so changing number of compilation jobs won't help, CPU can't go faster than 100%.
This blog introduces three mechanisms to investigate the execution time of a Maven build. Having a reliable way to measure build execution time can help identify bottlenecks. This in turn helps making effective improvements, thereby contributing to higher developer productivity. Find out how to effe...

Efficient containers with Spring Boot 3, Java 21 and CDS by Sébastien Deleuze @ Spring I/O 2024

YouTube Video
Click to view this content.
Yeah this survey is super inappropriate and offensive. Please do not ask such personal questions.
Did you notice that more inappropriate questions appear and disappear based on your previous answers?
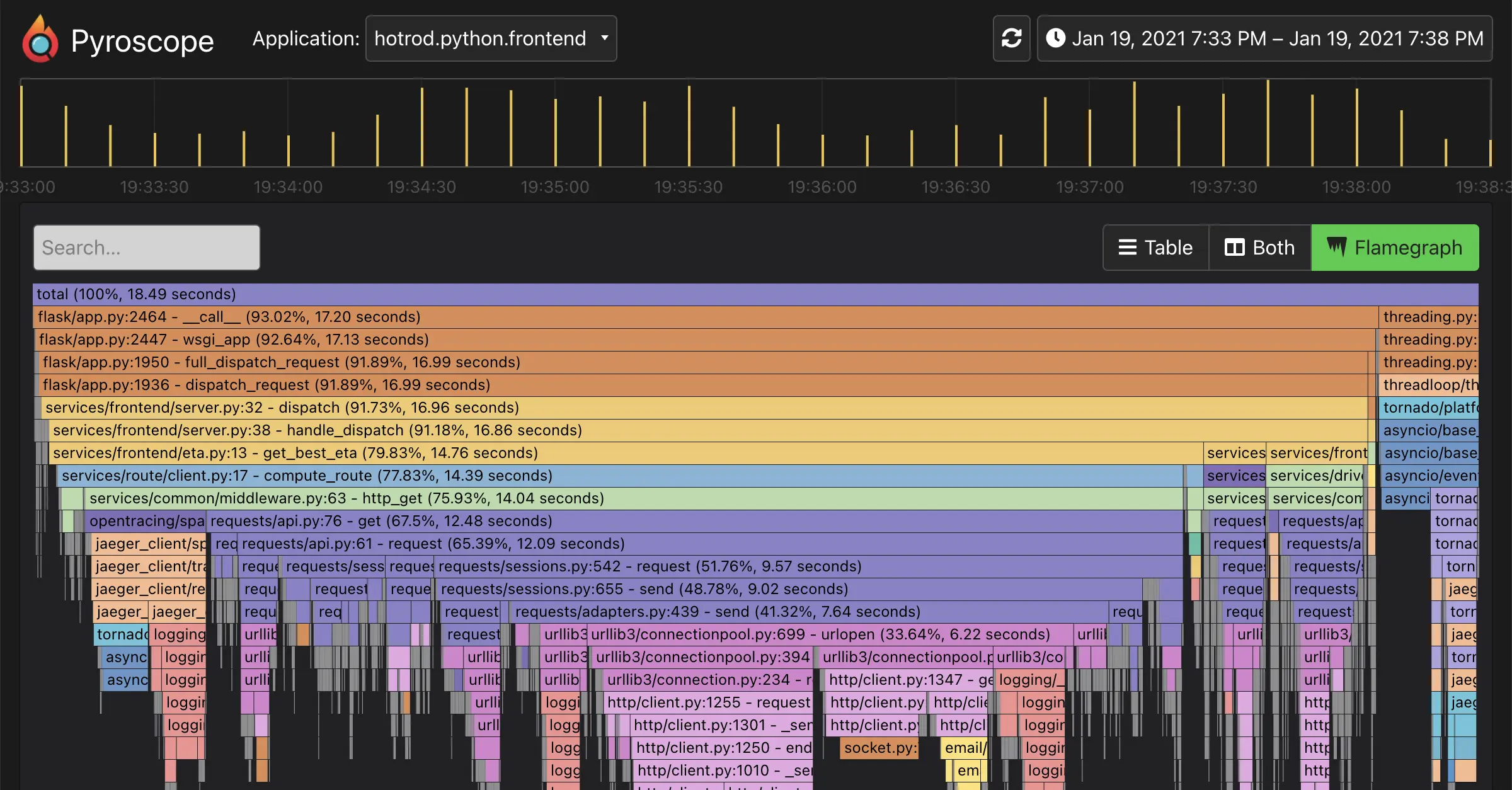
Explore how our AI-powered tool is revolutionizing flamegraph interpretation
Welcome to the Leyden Prototype Repo!
https://openjdk.org/projects/leyden. Contribute to openjdk/leyden development by creating an account on GitHub.
This is a lightly edited transcript of my presentation today at the ACCSS/NCSC/Surf seminar ‘Cyber Security and Society’. I want to thank the organizers for inviting me to their conference & giving me a great opportunity to talk about something I worry about a lot. Here are the original slides with ...
Using perf to profile Java applications
Find out how to use perf, a built-in Linux profiler, to analyze the performance of Java applications.
Old issue, so why post it now make it sound like MS demands something?
Opened 11 months ago Last modified 11 months ago
It's a regression, so ffmpeg should fix a regression.
It really depends on where you set the limit on what ORM is, JOOQ is kind of a thing you're looking for.
Nothing changed, openapi-genereator
I completely missed that user namespaces were added in 1.25. It will make homelabs much easier and safer with little effort.
Support user namespaces in pods (KEP-127)
User namespaces is a Linux-only feature that better isolates pods to prevent or mitigate several CVEs rated high/critical, including CVE-2024-21626, published in January 2024. In Kubernetes 1.30, support for user namespaces is migrating to beta and now supports pods with and without volumes, custom UID/GID ranges, and more!
https://kubernetes.io/docs/concepts/workloads/pods/user-namespaces/
After doing it for 15 years, I must be good at it and everything should be easy.
hidethepainharold.jpg
So while I'm myself struggling to fully understand what this is, it conceptually like it's a blockchain on syncthing, where even if you subscribe to a read only share, you can locally delete what you don't want to keep. So technically you could make bitorrent to behave like syncthing with search function for contacts you already know.


