cultural reviewer and dabbler in stylistic premonitions
It's getting harder to discern reality from satire, but Tim Onion has actually been The Onion's CEO's name* ever since he bought that job. And he is trying to buy InfoWars. (And the company formerly known as Twitter has joined Jones' fight to prevent it.)
*(his bluesky display name, at least)
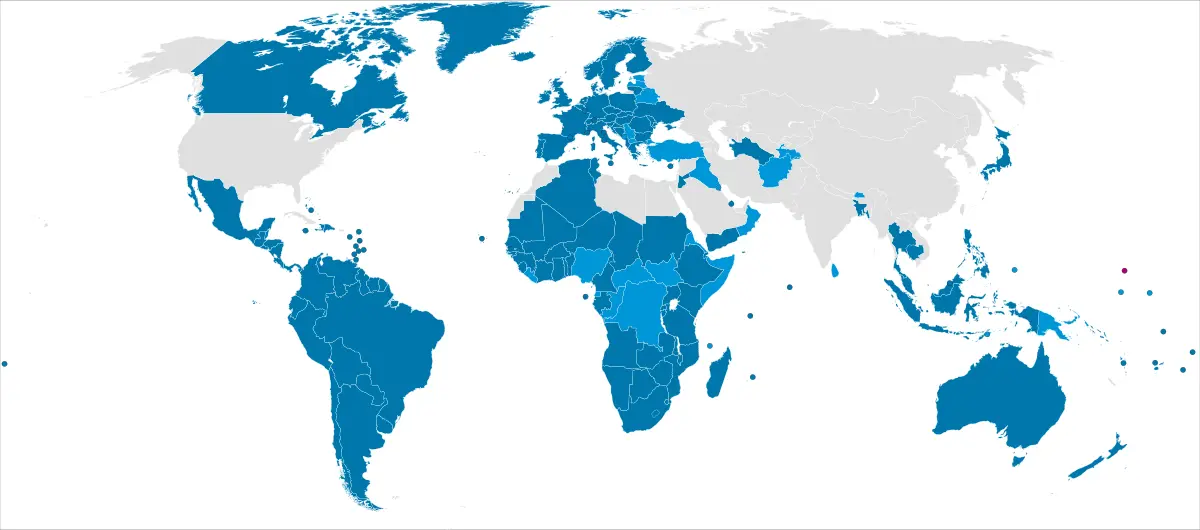
3rd place is too close to call between 🏇USA and 🏇China, while 🏇Denmark comes up from 130th place to beat 🏇Saudi Arabia for 12th! 🎠 (List of countries and dependencies by area)
But the race isn't over! 🍿 This was the latest version of the article at the time of this post, which the title is describing.
List of countries and dependencies by area: 3rd place is too close to call between 🏇USA and 🏇China, while 🏇Denmark comes up from 130th place to beat 🏇Saudi Arabia for 12th! 🎠
But the race isn't over! 🍿 This was the latest version of the article at the time of this post, which the title is describing.
I can't be the only Ersalrope Wars buff here, right?

and who really can go more than a few hours without thinking about the Koinonian Wars?

All three remaining US citizens classified by the State Department as wrongfully detained in China have been released, in exchange for the release of "at least one" Chinese citizen in US custody
The exchange was reportedly months in the making, and included the release of at least one Chinese citizen in US custody.

here is another report about it: https://www.scmp.com/news/us/article/3288409/3-americans-jailed-years-china-return-us
This add-on is not actively monitored for security by Mozilla. Make sure you trust it before installing.
It's pretty lame that Mozilla's addons site still doesn't show source code which is guaranteed to correspond to the binary you're installing.
Anyway, I went and read the source on github (which probably corresponds to the extension one can install) and while this part seems very straightforward this other part exceeds my understanding 😂 (i'm not suggesting it is malicious, i just don't understand everything it is doing there or why it is necessary).
What I was really looking at the source for was to see if they were simulating keystrokes (and inserting plausible delays between them) to defeat a more determined anti-pasting adversary, or if they were simply suppressing the hostile website's onPaste handler so that pastes can happen as normal. And: they are doing the latter.
I wonder if any paste-blocking websites detect and defeat this extension yet?
I can think of two ways: either using a password manager with a browser extension, or using the browser's built-in one.
bonus: make it something easy to remember, like your year of birth
I work in tech, and I don’t understand people’s obsession with having all their RAM free at all times.
If you don’t use it, why do you have it?
Windows (not the best OS, but the one I know the most about), will lie to you about how much memory you have that’s free. It puts data in RAM as cache. In the event you need that data, it’s already loaded in RAM. Usually this is stuff like DLLs and executables for programs.
There’s a difference between “free” memory, and “available” memory.
Linux and macOS do the same, although I wouldn't call it lying per se :)
There is certainly a lack of understanding of the difference between free and available RAM. TLDR: yes, free RAM is indeed wasted RAM.
If you actually have a lot of free RAM, it's probably because you either booted or freed a lot of RAM very recently. After using your computer for a while, most of your available RAM should not be free but rather being used for page cache and other caches.
After a program has just read and/or written more data from disk than will fit in available RAM, the kernel's page cache (which is typically the bulk of that not-free-but-available memory) should be mostly populated by the most recent of those operations. This means that if that program (or any other program) reads those files again, before they are evicted from cache by other things, they will not need to wait for the disk and will get them back much faster.
However, managing all of this is the kernel's job, and the not-free-but-available RAM being used for page cache is not (in any OS, as far as I know, though I mostly know Linux) attributed to the program(s) responsible for putting things there.
So, when people are complaining about an application using 40% of their RAM it is not necessarily due to them misunderstanding free-vs-available RAM. The used number for an application does not include the portion of the system's not-free-but-available RAM which the application is also responsible for occupying.
(If you want to know which programs and/or which files are responsible for occupying your page cache... on Linux at least, it is not really possible without instrumenting your kernel. The kernel is just tracking blocks. There several tools which will let you see which blocks of a given file are cached, but there isn't a reverse mapping from blocks to files.)
just in case Ars Technica has to remove it someday (perhaps for licensing reaasons? 😭), i am pasting a screenshot here of the excellent image illustrating this article:

Why would alphabetic order be involved at all?
Because the ... notation effectively means: fill in the blanks. See https://en.wikipedia.org/wiki/Ellipsis#In_mathematical_notation (or https://en.wikipedia.org/wiki/Iterated_binary_operation if you want more...)
(disclaimer: this information might be years out of date but i think it is still accurate?)
SSH doesn't have a null cipher, and if it did, using it still wouldn't make an SSH tunnel as fast as a TCP connection because SSH has its own windowing mechanism which is actually what is slowing you down. Doing the cryptography at line speed should not be a problem on a modern CPU.
Even though SSH tunnels on your LAN are probably faster than your internet connection (albeit slower than LAN TCP connections), SSH's windowing overhead will also make for slower internet connections (vs rsync or something else over TCP) due to more latency exacerbating the problem. (Whenever the window is full, it is sitting there not transmitting anything...)
So, to answer OP's question:
- if you want to rsync over SSH, you usually don't need a daemon (or to specify
--rsh=sshas that is the default). - if you the reason you want to use the rsync daemon is performance, then you don't want to use SSH. you'll need to open a port for it.
- besides performance, there are also some rsync features which are only available in "daemon mode". if you want to use those, you have at least 3 options:
- open a port for your rsync daemon, and don't use SSH (bonus: you also get the performance benefit. downside, no encryption.)
- setup an SSH tunnel and tell the rsync client it is connecting to a daemon on localhost
- look at
man rsyncand read the section referred to by this:-
The remote-shell transport is used whenever the source or destination path contains a single colon (:) separator after a host specification. Contacting an rsync daemon directly happens when the source or destination path contains a double colon (::) separator after a host specification, OR when an rsync:// URL is specified (see also the USING RSYNC-DAEMON FEATURES VIA A REMOTE-SHELL CONNECTION section for an exception to this latter rule).
-
HTH.
"someone who is good at the economy please help me calculate this. my battery is dying." ?
there are lots of good articles about this news from other sources.
unfortunately the link in this post is an advertorial for snakeoil: tuta published this for the sole purpose of marketing their non-interoperable encrypted email service which has an incoherent threat model.
Philippine Vice President Sara Duterte said Saturday she has contracted an assassin to kill President Ferdinand Marcos Jr, his wife, and the House of Representatives speaker, if she herself is killed
Under the Philippine penal code, such public remarks may constitute a crime and can be punishable by a jail term and fine.

they do not work for individual applications
as someone else replied to you earlier, waypipe exists, and is packaged in distros, and does what you're asking for.
There is also a newer thing called wprs, "Like xpra, but for Wayland, and written in Rust": https://github.com/wayland-transpositor/wprs#comparison-to-waypipe which sounds promising
i read it twice and somehow didn't notice the word "do" appears twice 🤡
"once in a lifetime event"? is this an effing joke?

seems rather defaming to say its invincibility and circular shape are "mysterious" when they're both established by law; maybe the volcano can sue The Sun? 🤔
Eerily circular rule


cross-posted from: https://lemmy.ml/post/22744127
> Sources: > * https://www.thesun.co.uk/news/31817061/perfectly-circular-invincible-goblin-forest-volcano/ > * https://en.wikipedia.org/wiki/Mount_Taranaki#National_park
Mystery solved


Sources:
- https://www.thesun.co.uk/news/31817061/perfectly-circular-invincible-goblin-forest-volcano/
- https://en.wikipedia.org/wiki/Mount_Taranaki#National_park
An open letter co-signed by over 50 international academics, including economists Thomas Piketty and Shoshana Zuboff, criticizes Elon Musk and Big Tech’s influence on Brazil's digital sovereignty.

If your car connects to the internet, what personal data could it be sharing – and even selling? A new report on Australia’s 15 most popular car brands reveals these privacy concerns.

cross-posted from: https://sh.itjust.works/post/28338848
> > New research reveals serious privacy flaws in the data practices of new internet connected cars in Australia. It’s yet another reason why we need urgent reform of privacy laws. > > > > Modern cars are increasingly equipped with internet-enabled features. Your “connected car” might automatically detect an accident and call emergency services, or send a notification if a child is left in the back seat. > > > > But connected cars are also sophisticated surveillance devices. The data they collect can create a highly revealing picture of each driver. If this data is misused, it can result in privacy and security threats. > > > > A report published today analysed the privacy terms from 15 of the most popular new car brands that sell connected cars in Australia.
President Biden is ramping up support for Ukraine in his final days in office with the provision of controversial anti-personnel landmines.

DOJ to ask judge to force Google to sell off Chrome, Bloomberg reports
The U.S. Department of Justice will ask a judge to force Alphabet's Google to sell off its Chrome internet browser, Bloomberg News reported on Monday, citing people familiar with the plans.
cross-posted from: https://sh.itjust.works/post/28293258
> Note: Original report by Bloomberg, article by Reuters proxied by Neuters to bypass paywall.
Thousands are marching against a bill they believe undermines the Treaty of Waitangi and limits Maori rights.

US President-elect Donald Trump has campaigned on a promise to end America's involvement in wars.

RFK Jr. Says He’ll Send People Taking Adderall to Labor Camps
Robert F. Kennedy Jr. wants to strip people of their tech gadgets and send them to government-funded "wellness farms" to grow organic food.

Israelism: The awakening of young American Jews (80 minute documentary)
YouTube Video
Click to view this content.